Kaseya VSA Supply-Chain Attack: Everything We Know...so far
On July 2nd, 2021, the IT management software company, Kaseya, disclosed to the public that they had a security incident on their hands impacting their on-premises version of Kaseya's Virtual System Administration (VSA) platform. Kaseya VSA is a cloud-based MSP platform used by customers to perform patch management and monitoring for clients.
The company issued a security advisory warning customers to immediately shut down their VSA server to keep from propagating the malware.
"We are experiencing a potential attack against the VSA that has been limited to a small number of on-premise customers only as of 2:00 PM EDT today. We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us. Its critical that you do this immediately, because one of the first things the attacker does is shutoff administrative access to the VSA."
Security researchers, like John Hammond of Huntress, have attributed the ransomware deployments on what appears to be a supply-chain attack leveraged through Kaseya's VSA. The Kaseya VSA software drops an agent.crt file to the path < OS_Installed_Partition >:\kworking, distributed as an update titled 'Kaseya VSA Agent Hot-Fix'. Once this is done, a PowerShell command is executed that disabled multiple Microsoft Defender features like real-time monitoring, script planning, network protection and Controlled Folder Access. It then decodes the dropped agent.crt file using built-in Windows certutil.exe to extract agent.exe. This is then launched to begin encryption of the drive.
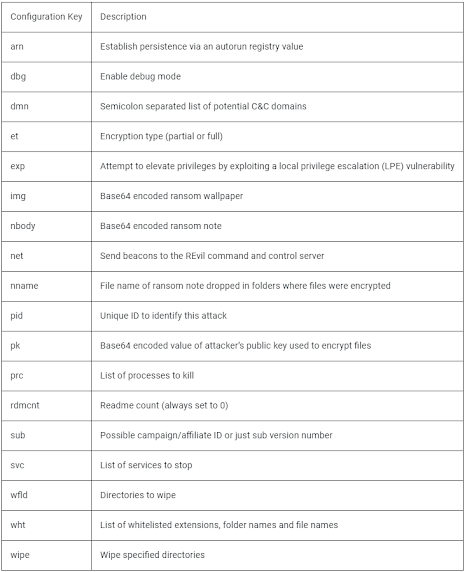
Signed by "PB03 TRANSPORT LTD", agent.exe includes an embedded "MsMpEng.exe" and "mpsvc.dll"; the latter of which being the REvil encryptor. Once these are extracted, both entities are placed in the < OS_Installed_Partition>:\Windows. TheMsMpEng.exe is a legacy version of a legitimate Microsoft Defender executable used as a LOLBin to execute the encryptor DLL and encrypt the drive(s) through a trusted executable.This particular variant of REvil ransomware leverages multiple techniques to evade security controls. The malware is using a customized packer with the REvil payload being distributed as a portable executable with a modified header. This is most likely done to circumvent security products that are not capable of properly handling portable executable files that have been altered. The variant's binary has an embedded encrypted configuration, using RC4 at runtime. This configuration houses settings for the malware and is stored in a JSON format with the following parameters:
REvil will encrypt files not contained in the whitelisted filenames fields (stored in configurations). The malware reads each file before encrypting the contents and writing the results back to the original file to prevent recovery. Once encryption is finished, a footer is written to the end of each file and the encrypted file is renamed using a new extension. REvil combines use of Curve25519 (asymmetric) and Salsa20 (symmetric) encryption algorithms. Salsa20's encryption key is derived from the target's public key and secret key of the pair created for each file. In order to decrypt the files, the victim's secret key and file public key have to be known. REvil writes a footer that is 232 bytes (0xE8) at the end of every file and contains the following metadata:
Indicators of Compromise
https://www.bleepingcomputer.com/news/security/revil-ransomware-hits-1-000-plus-companies-in-msp-supply-chain-attack/






Comments
Post a Comment